Features
Business
Protect your business from cybercrimes
Here are some strategies to safeguard printing companies from cyberattacks
November 24, 2023 By Grant Sadler, P.Eng
 Printers can often be targets of cyberattacks, so protect yourself. Photo © adam121 / Adobe Stock
Printers can often be targets of cyberattacks, so protect yourself. Photo © adam121 / Adobe Stock In today’s fast-paced business world, the printing industry faces several technological challenges, including the ever-present threat of cyberattacks. As more and more processes go digital, the importance of ensuring robust cybersecurity in the printing and imaging sectors cannot be overstated. In this article, we will explore the challenges and opportunities related to cybersecurity in the printing industry and discuss best practices that can be adopted to help keep businesses safe.
Challenges
The printing industry faces several unique cybersecurity challenges. Firstly, printers, as networked devices, can often be targets of cyberattacks, as they may have access to sensitive and valuable information. Secondly, the complexity involved in securing various components of a printing business, such as email systems, company websites, social media accounts, backend systems (billing), online banking, mobile devices, and remote access, can pose a challenge for businesses that may not have dedicated IT security teams.
Opportunities
Despite the challenges, businesses in the printing industry have the opportunity to address their cybersecurity needs proactively. By leveraging advanced security solutions and adopting best practices, organizations can minimize the risk of cyberattacks and, consequently, protect their reputation and valuable information. Further, by demonstrating a high level of cybersecurity maturity, printing companies can attract new customers who value data privacy and security.
Phishing attacks
A common cybersecurity threat that many businesses face is phishing, which involves cybercriminals attempting to gain access to sensitive information by posing as a trustworthy entity. For example, an attacker may send an email to an employee of a printing company, pretending to be a client, with a suspicious attachment or a link to a website that installs malware on the user’s computer. If the recipient opens the attachment or clicks on the link, the attacker may gain unauthorized access to the company’s systems and compromise crucial information, potentially leading to financial or reputational loss.
To counter phishing attacks, printing companies can train their employees on how to recognize potential phishing emails, encourage the use of strong, unique passwords for each account, and use multi-factor authentication methods to protect critical systems and information.
Ransomware attack
Ransomware is a type of malware that encrypts a victim’s data and demands payment, usually in cryptocurrencies, to release the decryption key. In this example, a cybercriminal infiltrates the network of a printing and imaging services provider and deploys ransomware, effectively locking the company out of its critical files and systems. Until the ransom is paid, the company cannot access its data or fulfil customer orders, causing significant operational disruption and revenue loss.
To protect their businesses from ransomware attacks, printing companies should ensure all software on their systems is up-to-date and patched regularly, as outdated software can present vulnerabilities that cybercriminals exploit. Additionally, implementing robust data backup and recovery processes and educating employees on cybersecurity best practices can significantly reduce the risk of falling victim to ransomware attacks.
Cyber hygiene
To protect from ransomware and other cyberattacks, all employees and contractors should take ownership of their cyber hygiene and follow these best practices:
1. Always use strong authentication for credentials on all software and systems:
- Enable MFA (multi-factor authentication)
- Authenticator app is more secure than SMS
- Enable biometrics
- No passwords to lose or share
- Make all passwords unique and complex
- 15+ characters long
- When a password is compromised, only one account is affected
- Use a password manager
- Use Passkeys
- Severely reduces social engineering effectiveness
2. Never join an unknown network, like a free wi-fi network. This leaves your device open to any other device on the network.
- Most public networks are big “flat” networks, which are a hacker’s dream
- Hotspotting to a cell phone is better
- Bringing your own router/gateway is the best
3. Keep all software and applications up to date. Out-of-date software often contains vulnerabilities that hackers exploit to infiltrate networks and systems.
- Enable auto-update
- Restart your browser (most browsers auto-update, but they need to be restarted to take effect)
For IT professionals and more advanced users, the following should also be done:
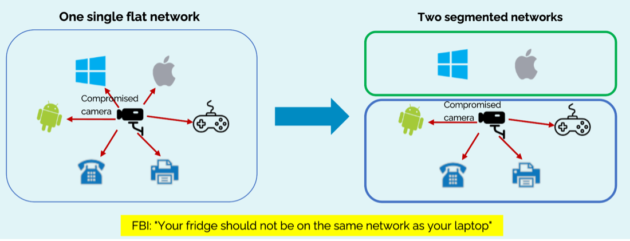
4. Segment your network. Dividing a company’s network into smaller, isolated segments will minimize the risk of a cyberattack spreading to other systems because it restricts the attacker’s lateral movement. This can be achieved by the following methods:
- Separate router/gateway
- VLAN
5. Enable threat and phishing protection by using a DNS provider that has a better “phone book” that doesn’t include “phone numbers” (IPs) for bad actors. When users click on a “bad” link in an email, this will stop the attack in its tracks. Additionally, malware trying to “call home” to some rogue domain won’t be able to get there.
- Can be configured on your home router – best
- Can be configured on each end-point device or even in each browser
- Free DNS providers
- OpenDNS
- CIRA Canadian Shield
6. Continuous traffic monitoring and inspection, while maintaining full employee privacy
- Do not decrypt traffic – packet inspection can be done without decrypting packets
- Implement advanced network monitoring and threat detection tools
Conclusion
The printing industry faces unique cybersecurity challenges, but also has the opportunity to address these issues proactively. With all users taking ownership of their own cyber hygiene and adopting best practices, such as strong authentication, regular software updates, and making sure not to join unknown networks, the risk of cyberattacks is reduced drastically. Additionally, with corporate IT professionals adopting network segmentation, threat and phishing protection, and continuous monitoring and response, any potential threat will be contained and easier to eliminate.
Grant Sadler, P.Eng, has 17 years of telecom experience, having held various technical and management roles at TELUS in Toronto. He then founded and ran a home automation and security company for seven years before joining CyberLucent in 2021.
This article originally appeared in the September/October 2023 issue of PrintAction.
Print this page